The goal of penetration testing is to find and exploit vulnerabilities in a computer system with the help of a cyber-security expert. Simulating an attack in this way helps identify any weak points in a system’s defences that attackers could exploit.
It is like a bank hiring someone to dress as a burglar and try to break into their building and access the vault. The bank will gain valuable information about strengthening its security measures if the ‘burglar’ succeeds in getting into the vault or bank.
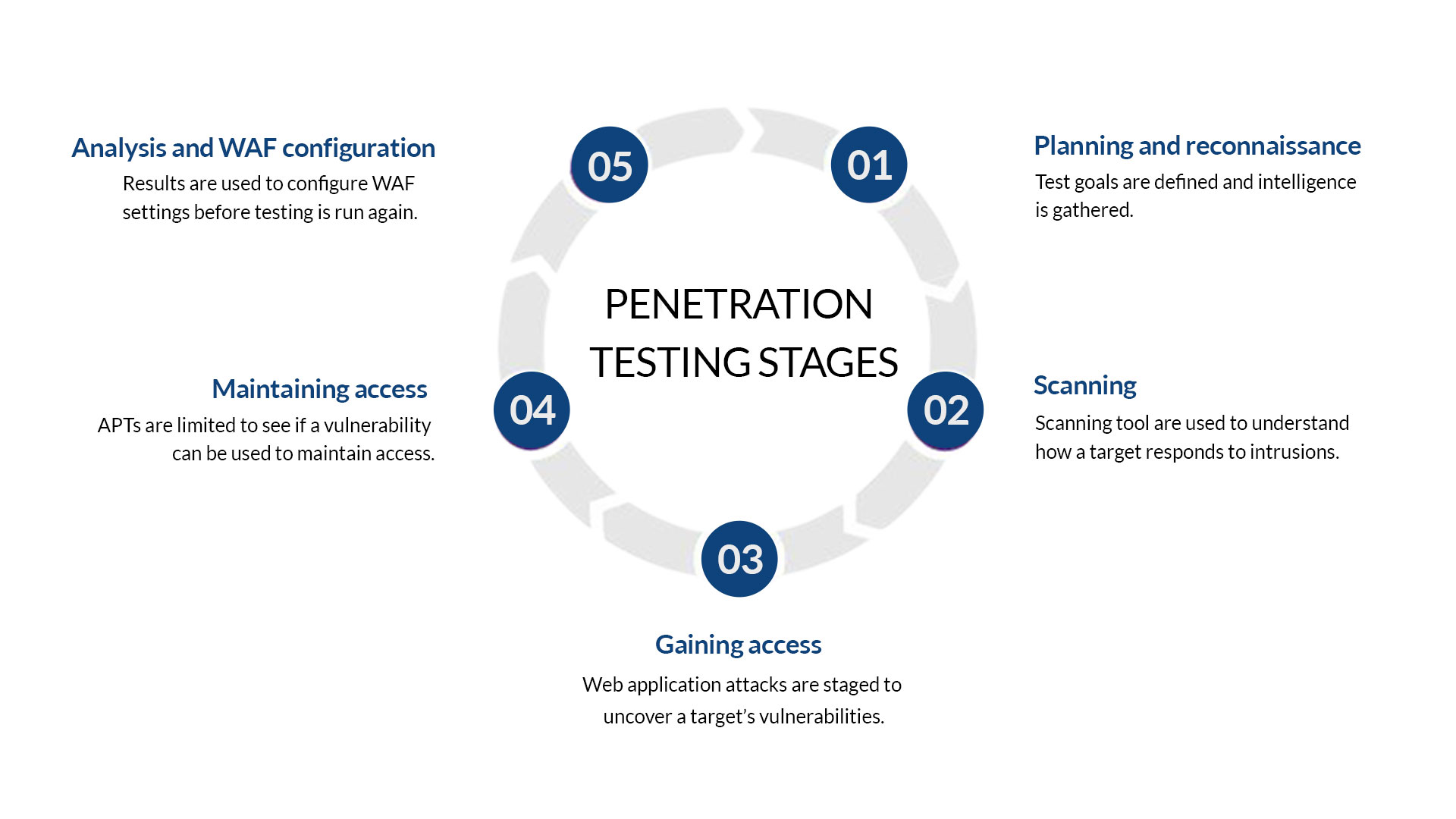
Penetration testing stages
It can break down the pen testing process into five stages.