Security for cloud computing environments, applications, data, and information is a discipline and practice concerned with protecting the data, information, and applications associated with cloud computing. Among the risks associated with cloud security include unauthorized access to/use of cloud environments, DDoS attacks, hacker attacks, malware attacks, and other threats. Cloud security pertains to cloud environments, but cloud-based security refers to security delivery via software as a service (SaaS) rather than hardware or software deployed on-premises
Cloud security
Cloud security
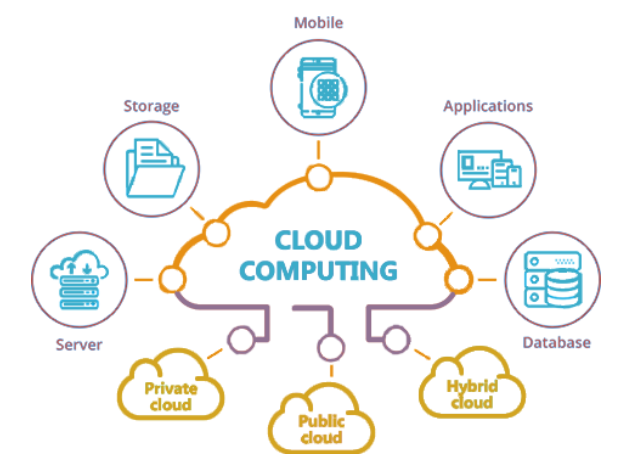
We can categorize cloud environments into three types:
Cloud computing services for the public
Third-party cloud service providers host them (e.g., Amazon Web Services, Microsoft Azure, Google Cloud) and are typically accessible via web browsers, making authentication, access control, and identity management crucial.
The Private Clouds
There are often only one or a few companies that have access to them. Despite these measures, they remain vulnerable to access breaches, social engineering, and other attacks.
The Hybrid Cloud
Hybrid cloud technology allows organizations to take more control over their data and resources than they would in a public cloud. It is because they have access to the scalability and other benefits of the public cloud as needed.
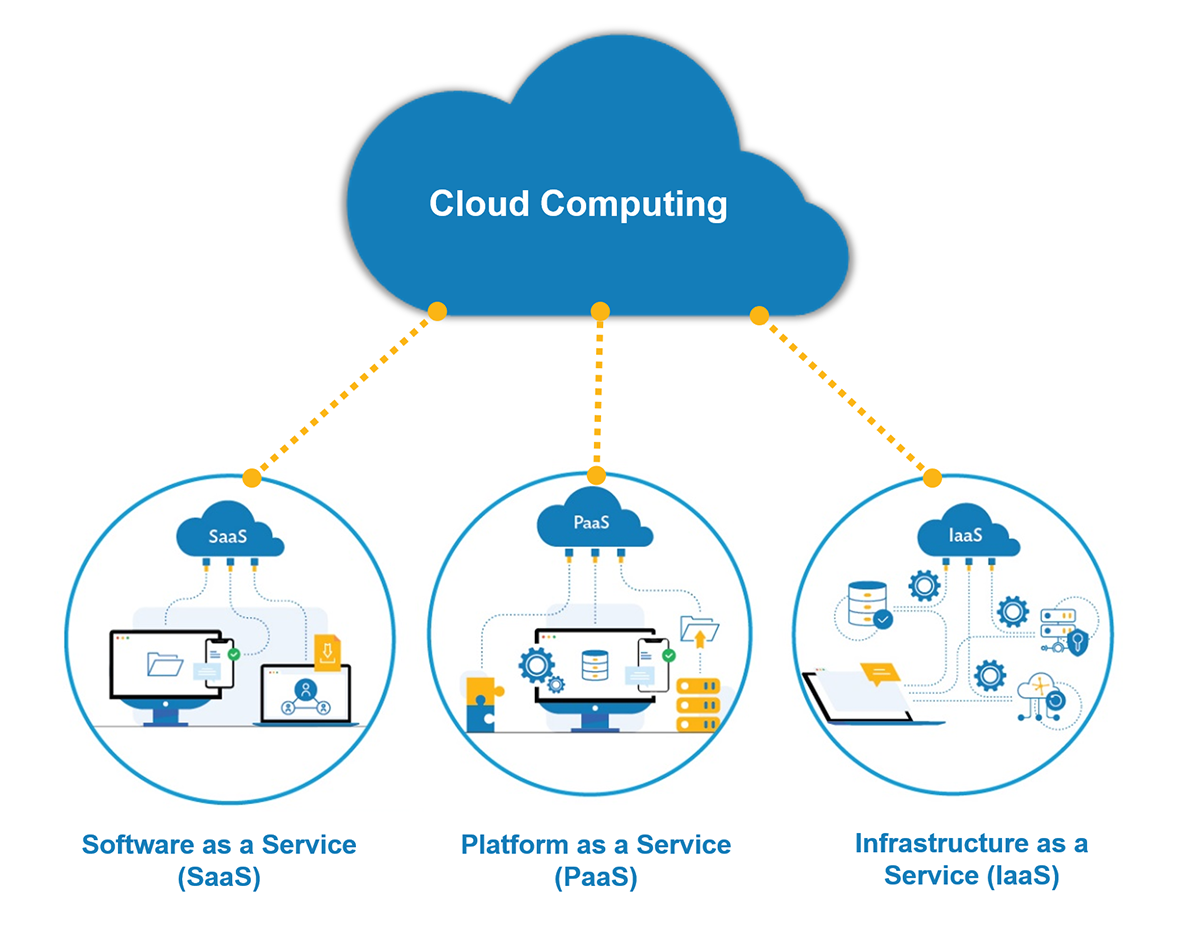
Cloud service models fall into three categories:
The Infrastructure-as-a-Service (IaaS) model
It enables an on-demand model for pre-configured virtualized data center computing resources (i.e., network, storage, and operating systems). A scalable, automated virtual machine creation process is crucial, and it’s essential to consider the provisioning, management, and spindown of virtual machines.
PAAS “Platform as a Service.”
Tools and other computing infrastructure are provided to organizations to create web services and applications. PaaS environments typically support DevOps, operations, and development teams. Risk control depends on effectively managing and configuring self-service entitlements and privileges.
“Software as a Service” SaaS
It consists of applications hosted by a third party. SaaS usually delivers software services over a web browser accessed on the client’s side. Putting an end to installing applications and managing them on end-user devices, SaaS allows any employee to access web services and download content. The proper visibility and access controls are needed to monitor the kinds of SaaS applications used, their usage, and cost
Capabilities
Achieving security in the cloud includes four steps with “We Secure” Cloud Security capabilities.
Understand your security posture
It establishes a baseline cloud security architecture and road map that optimizes existing technology investments that quickly uncover gaps.
Integrate native security automatically
It doesn’t take long to get value from cloud services, including AWS, Microsoft Azure, and Google Cloud. You can automate the deployment of security guardrails.
Make compliance a priority
Detect cloud threats more effectively and streamline cloud security operations. Ensure that cloud service providers (CSPs) adhere to regulatory requirements by managing their risks.
Utilize security monitoring and response techniques
Security tools and use cases provide low-cost and scalable monitoring of public clouds to meet evolving threats and complex regulatory requirement
